KLogix:Cyber Security Business Podcast
On this episode of Cyber Security Business, we sit down with John Masserini, CISO, Millicom, to discuss identity and access management in the current security environment. Excerpt: Kevin West: Welcome…
Fahrenheit 451 – Security Research Edition
In 1998, the US passed The Digital Millennium Copyright Act (DMCA) in an effort to enact several of the requirements of World Intellectual Property Organization (WIPO). DMCA makes it a…
The Identity Catechism: Questions every CISO should ask of their Identity program
The evolution is underway. Our infrastructures are borderless, our critical data is cloud-based, and our users work from anyplace on the globe – or 36,000 feet above it. Our legacy…
SecurityWeek: Quest for Cybersecurity Metrics Fit for Business
Developing clear, well defined cybersecurity metrics are necessary for the business lines to understand the risk they face. Therefore, it is often a challenge because technical risk doesn’t always relate…
A Contrarian View of the NIST Digital ID Standards
Recently, while attending a conference in DC, I was part of a discussion around the new NIST Digital Identity Guidelines (SP 800-63) and how “…it turned the password world upside…
Whitehawk: 10 Rules for Cybersecurity Salespeople
I’m posting this for two reasons. First, it’s a great read for security vendor’s salespeople. You need to memorize these rules. Secondly, and I have to be honest, I’m pretty…
Why Diversity Matters in Leadership
As I write this, it is the celebration of Alan Turing’s 106th birthday (June 23, 1912). As someone who wears their Geek Badge proudly, one has to wonder what the…
Klogix: Profiles in Confidence – John Masserini
Truly honored to be a featured CISO in the Klogix Profiles in Confidence magazine. Feats of Strength is a business-focused information security magazine created by K logix. They provide a…
Ethisphere/Opus: Risk Management as a Team Sport
Honored to be included in this multi-topic whitepaper on how to manage risk throughout the enterprise by partnering with your business lines. In this special Risk Management report by Ethisphere…
Radware: Places to find cybersecurity talent
An interview with Radware around identifying cybersecurity talent in unexpected places within your enterprise. Companies are scrambling to fill cybersecurity positions. Some 41 percent of CIOs surveyed by recruiting firm…
SecurityWeek: Fighting CyberSecurity FUD and Hype
An interview with SecurityWeek around how FUD permeates the cybersecurity industry and how security vendors use it to sell unnecessary products. Increasingly, vendors have come under scrutiny with the never…
TechTarget: Security’s role in business continuity
TechTarget interview around aligning Crisis Management and Business Continuity with the control structures of the organization. All CISOs have responsibilities and pressures that make the job fun, interesting and sometimes…
CSOonline: Should security pros get special H-1B visa consideration?
An interview with CSOonline around the hiring challenges the security industry continues to face. New U.S. Attorney General Jeff Sessions may disagree about whether there is a shortage of skilled…
SecurityCurrent: CISOs Investigate: User Behavior Analytics
The report includes an overview of the technology, staffing implications, recommendations for selling User Behavior Analytics (UBA) to the C-Suite and possible objections. It also features a market assessment based…
SC Magazine: Diversity, one key to solving cybersecurity job gap
I recently had the honor of participating in an IBM/International Consortium of Minority Cybersecurity Professionals (ICMCP) event in Manhattan. This is coverage of the panel I was on which discussed…
The Army of Things in an IoT World
The Internet of Things is here.. By now, you’re probably well aware of the fate recently befallen on the Brian Krebs site KrebsOnSecurity.com. A Distributed Denial of Service (DDoS) attack…
SecurityCurrent: Podcast with Barmak Meftah, President and CEO AlienVault, About Threat Detection and Response
In this conversation, MIAX Options CSO John Masserini discusses the threat detection and response space with AlienVault President and CEO Barmak Meftah. An early adopter of threat intelligence, Masserini notes…
SecurityWeek: Inside The Competitive Testing Battlefield of Endpoint Security
Interview in SecurityWeek around the pros/cons of legacy antivirus endpoint and next-gen antivirus endpoint solutions. There is bad feeling between what can be described as traditional antivirus (Trad AV) and…
SecurityInnovation: CISOs Guide to Application Security
As infrastructures become increasingly fragmented and distributed, the need for a strong application security program becomes more and more critical. Cloud-based hosts, server-less architectures, and Applications as a Service require…
The Little Green Devil – Android GODLESS has arrived
Consider this if you will, that at the end of 2015, Google estimated there were 1.4 billion Android devices in use worldwide, and its over 2 billion devices when you…
SC Magazine: Case study on Privileged Access
The MIAX Security team was honored to be a case study on deploying a real-world, fully integrated Privileged Access Management solution. The MIAX Options Exchange needed more than a way…
Privileged Account Management: A BeyondTrust Case Study
A case study on the enterprise-wide deployment of a fully integrated privileged account management solution, the potential deployment challenges, and the numerous post-deployment security and productivity benefits. Challenge: Provide Regulatory…
The Best Security Control You Never Use
Consider for a moment the business lines that drive your company’s revenue. If the president of that business unit had an 85% assurance that a new business venture would be…
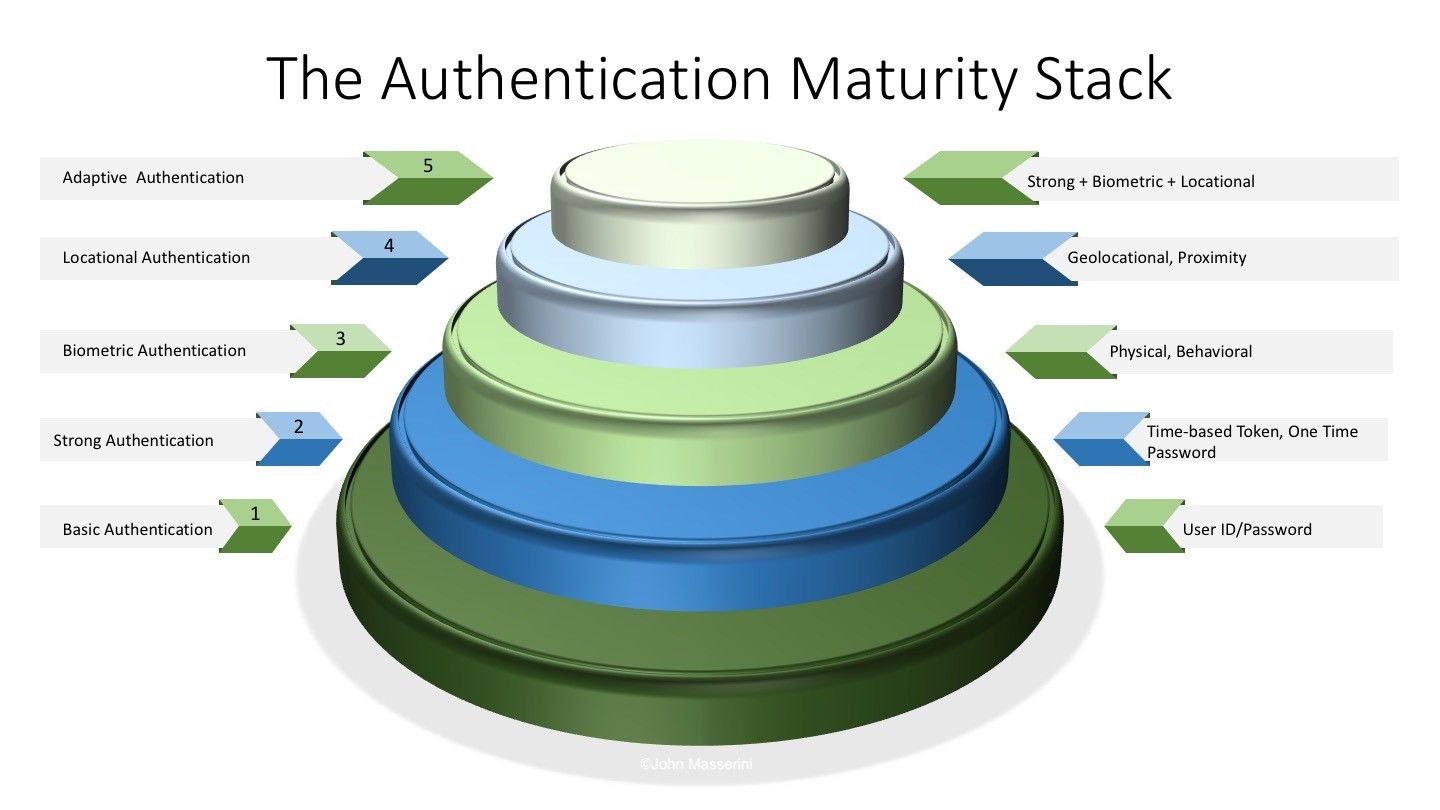
The Current State and Future of Biometrics
Recently, I had the opportunity to sit down with Morey Haber, VP of Technology, BeyondTrust to discuss the future of biometrics and the role it played in advanced authentication techniques.…