CSNP: How Working From Home Is Changing The Business Environment
I recently had a wonderful opportunity to sit in on a panel discussing how the pandemic is going to change the way security practitioners think about protecting their organizations.
BeyondTrust: CISO Diaries
I had the honor of participating in the LinkedIn Live event on some of the scarest things I have ever heard from my security team.
CISO 101: How to Walk & Talk Like a CISO
I had an opportunity to reflect on what is takes to be a CISO, how I got here, and where I think the industry is heading.
Ed Talks: Kicking 3rd-Party Software Risk to the Curb
Panel discussion on third-party risk. Topics included conducting software composition analysis (SCA), assessing threats and impacts, risk-rating your inventory, and selecting the right controls.
Companies Battle Another Pandemic: Skyrocketing Hacking Attempts
An interview with the Wall Street Journal around the rapid uptick in enterprise attacks seen amongst the initial weeks of the COVID-19 outbreak.
Companies Rush to Implement Identity Systems for Remote Working
An interview with the Wall Street Journal around the need for an effective identity management solution to manage the rapid growth of the remote workforce.
Diversity Resources to Make a Change
In holding myself accountable to my own call-to-action, I have dedicated a page to share all of the diversity-centric resources I have collected over the years. From How-To guides to…
Dark Reading Usability Interview
An interview I did with Ericka Chickowski of DarkReading on the importance of useability of security products.
Let’s Use This Outrage to Make a Change
The outrage over the George Floyd murder is causing many to push for change. Will you use your outrage to fix the diversity issues you see every day?
2020 Best New Blog – Security Bloggers Awards
Chronicles of a CISO was named 2020 Best New Blog of the Year by the Security Blogger Network
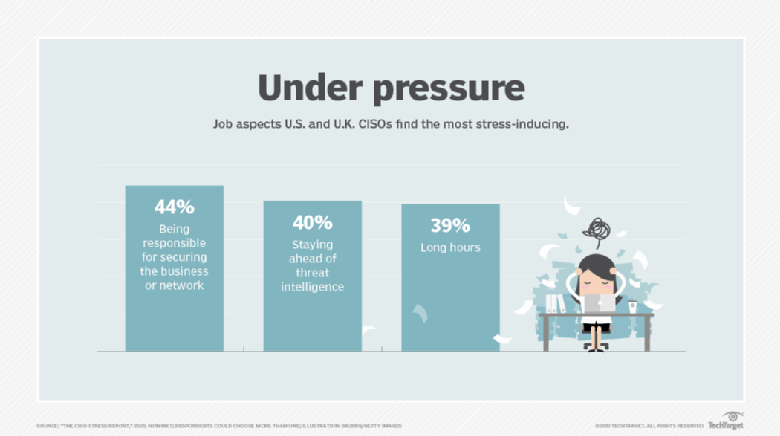
CISO position burnout causes high churn rate
A recent interview I did with SearchSecurity/TechTarget. While much was about the benefits and love of the job, the 'job churn' and 'burnout' discussions are front and center in the…
Free COVID-19 Resources
This page will list various personal and family-related ‘remote’ STEM activities to participate in as well as other free offerings to help companies, individuals and families cope with their newfound…
A Few Leadership Work-From-Home Tips
With so many people now being asked to work-from-home as part of the evolving COVID-19 precautions, I figured it was worthwhile to put together a few tried-and-true practices to keep…
A Few Leadership Work-From-Home Tips
A few tried-and-true practices to keep you productive and sane while spending an unexpected few weeks in the home office.
Tech Hiring is Badly Broken
As a hiring manager, how does someone make a person go through three video interviews, do two coding assignments, be so impressed with the coding that they then fly the…
The First Anniversary of Chronicles of a CISO
It’s hard to believe it’s been a year already. Twelve months ago, I took the leap and decided that it was time to start my own blog, and now, here…
Identity Attack Vectors, by Haber and Rolls
Honored to have had the privilege to write the forward to the third book of Morey Haber‘s trilogy of enterprise attack vectors. This installment, written with Darran Rolls, discusses the…
3 Fundamental Questions to Ask of Your Identity Program
This is an abbreviated version of my Identity Catechism piece that I wrote in early 2019. This piece focuses on the three key topics to focus on when planning and…
When Security Metrics Miss The Point
After countless years of presenting to boards, executives, and colleagues, I’ve found that I’ve developed almost a split-personality when I’m asked about what metrics to track.
Q&A with John Masserini, Global CISO at Millicom
This is an interview with George Hulme is an internationally recognized writer who has been covering the technology and information security space for more than 20 years, with pieces appearing…
Two-factor Authentication Is Not Dead
I’ve had just about enough of the fear mongering and lazy ‘reporting’ that’s been in the press recently around how two-factor authentication is broken. I’m not sure about you, but…
RSA Sales & Marketing Panel on Relationships
For a number of years, I’ve had the honor of participating on the T.E.N. ISE® Sales and Marketing Breakfast panel at RSA. This year’s panel included some of my most…
How to Personalize Your Product Pitch for CISOs
A Q&A with John Masserini, CISO at Millicom Telecommunications This Merritt Group blog is part of an ongoing Q&A series with CISOs on preferred marketing and sales techniques, leading up…
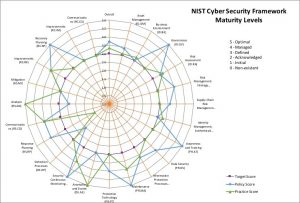
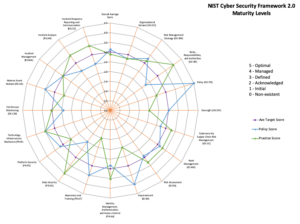
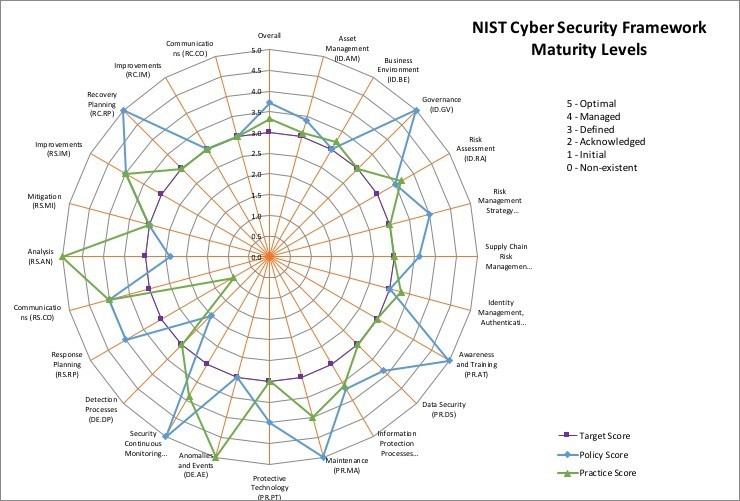
Free NIST CSF Maturity Tool
In my previous post, ‘My Three Wishes for 2019’, I had wished that we all find a way to give back to the industry, even a little bit. In an…
My Three Wishes for 2019
It’s the end of the year and like all of you, my news feed has been filled with ‘Predictions for 2019’ to such a point that I basically ignore them.…