Estimated Reading Time: 3 minutes
I have been attending the RSA Conference fairly regularly since the mid-1990’s, but this year, I had the distinct privilege of presenting there for the first time. As I mentioned on my LinkedIn post, I was completely blown away by the near-capacity attendance, especially for something so… mundane as the NIST CSF Maturity Toolkit.
When you walk the show floor, its easy to get the impression that tech can solve the security’s problems, but most practitioners know that couldn’t be further from the truth. While technology solutions are a key element in the CISO’s toolkit, they are hardly effective without the solid underpinnings of a well-designed and well-implemented set of controls.
The NIST CSF is arguably one of the best defined, highly flexible frameworks that provides this foundation, regardless of organization size or industry. Unlike some other overly-prescriptive frameworks, the CSF allows the flexibility to develop controls that fit your business, rather than adjusting your business to fit the framework.
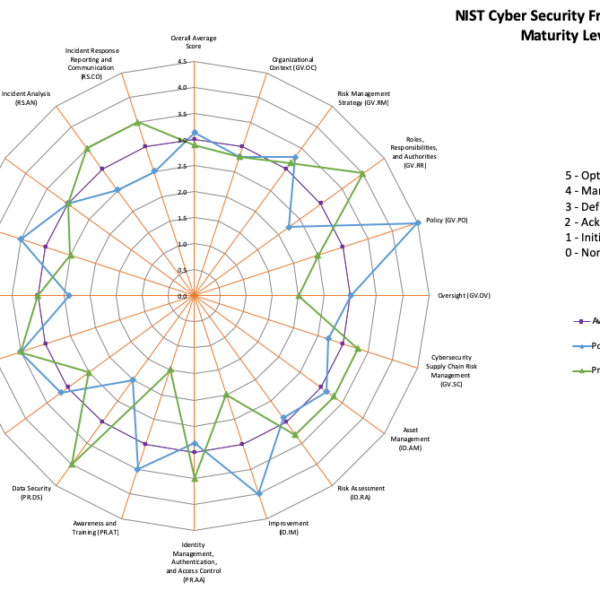
The one thing the CSF does not do well is provide a way to measure the maturity of the implemented control set, and that’s where the NIST CSF Maturity Toolkit comes in (read more here). The Maturity Toolkit was been downloaded over 30,000 times since I originally published in back in 2015.
My RSAC session was focused on how to use and leverage the Maturity Toolkit to measure your overall level of maturity and track that progress over time. Not only was the room packed, but there was great interaction with the attendees and discussions that overflowed into the hallway for 45 minutes afterwards.
You can watch the recording of the session using the button below. It will require a RSA Conference account, but its free to make one if you didn’t go to the conference. You can also download the presentation from the repository.
As always, I’d love to hear your feedback!






Copyright © 2002-2025 John Masserini. All rights reserved.