Estimated Reading Time: 6 minutes
This page is a catalog of all publicly available content that I have developed for TAG Cyber.

October 2, 2023
Tag Cyber: The Evolution of CSPM
The existing cloud security space is flooded with single-issue solutions (security posture management, data security, vulnerability management, etc.) that do little to provide a security team with insight into the overall risk of an enterprise’s cloud environment, and what should be done about it. Multi-cloud environments, along with hybrid clouds, are posing challenges to many of the cloud security solutions on the market today.
In this report, we will review the challenges of securing a modern cloud-based infrastructure and why a comprehensive, real-time discovery and alerting solution is needed.
Download The Report: PDF

August 29, 2023
Tag Cyber Webinar: The Evolution of CSPM
As cloud computing continues to reshape the modern IT landscape, the approach to cloud security must also undergo a seismic shift. Over the years, cloud security posture management (CSPM) has undergone a remarkable transformation, adapting to the ever-changing needs of cloud-native environments.
Throughout this session, we will analyze the pivotal milestones that have shaped the evolution of CSPM, from basic configuration checks to sophisticated behavioral threat detection and beyond. Then, we’ll speculate on what the future holds and how CSPM can keep evolving to address future cloud and cloud-native security challenges.
Watch the replay: Webinar

August 17, 2023
Tag Cyber: Adding File Security to Your Email Platform
Since 2018, the user base of Microsoft Office 365 has steadily grown from 155 million to more than 345 million in 2022. Unlike Google’s Workspace, whose growth was predicated by a free email platform, Microsoft’s growth is founded in the migration of large-scale enterprises moving from legacy on-premise Exchange environments to a cloud-based, O365 experience.
Read the blog: Votiro Blog
July 27, 2023
Tag Cyber: Accelerating Cybersecurity Compliance With Mean Time to Compliance (MTTC)
Watch this webinar-on-demand to hear from operational security leaders discuss the opportunities generative AI represents to security teams, the practicality of the challenges teams face today, and where we are as an industry in our readiness to manage both
Watch the webinar: Webinar Replay

July 17, 2023
Tag Cyber: Accelerating Cybersecurity Compliance With Mean Time to Compliance (MTTC)
As organizations increasingly migrate to cloud computing solutions to streamline IT operations and reduce costs, ensuring the security and integrity of sensitive data becomes paramount. However, achieving compliance can be complex and challenging. This whitepaper details how RegScale, the world’s first real-time governance, risk and compliance (GRC) platform, specializes in helping organizations achieve compliance with multiple cybersecurity frameworks
Read the paper: PDF

July 11, 2023
Tag Cyber: The Threat Show Ep. 34
Christopher Wilder, Darien Kindlund, and I discuss how many organizations underfund their security teams, increased regulations that are changing how CISOs think, six trending threats, and more.
Watch the podcast: The Threat Show Ep. 34

May 3, 2023
Tag Cyber: Aqua CISO Panel – Tips for Optimizing Your Cloud Native Security Stack
Joe Murphy, Ira Winkler, and I discuss the best ways to evaluate your current cloud security stack, how to optimize the tools you have, and some of the leading, effective cloud-native security practices.
Watch the video: Tips for Optimizing Your Cloud Native Security Stack

April 19, 2023
Tag Cyber: RSA Roundup
James Rundle’s RSA roundup. Vendor consolidation, Market cooldown, and Bridging the public-private sector gap.
Online: WSJ Pro RSA Roundup PDF Version
March 6, 2023
Tag Cyber: Flipping the Paradigm – Data Defense as a Business Opportunity
In this webinar, Roland Cloutier, Ari Weil, and I discuss flipping the paradigm from defense against an adversary to offensively seizing the opportunity for data to transform and accelerate business outcomes.
Watch the podcast: Cyera – Flipping the Paradigm

February 16, 2023
Tag Cyber: Content Disarm and Reconstruction – What It Is and Why It Should Be in Your Toolbox
This report for Votiro highlights the role a modern content disarm and reconstruction solution plays in the enterprise and how such an approach is invaluable against today’s threat actors.
Read the full report: Content Disarm and Reconstruction – What It Is and Why It Should Be in Your Toolbox

November 29, 2022
Tag Cyber: Transforming Attack Surface Management as a Keystone to Modern Security
This report, for Noetic Cyber, discusses the challenges of legacy approaches to Attack Surface Management, how to modernize the approach, and how it can become a foundation for a modern security program.
Download the full report: Transforming Attack Surface Management as a Keystone to Modern Security

October 25, 2022
Tag Cyber: Quarterly Report
As part of our Quarterly Report series, this report focuses on Cybersecurity Metrics, identifying good ones and ensuring the correct messages are getting across.
Download the full report: TAG 4Q2022 Cybersecurity Metrics.

October 3, 2022
Tag Cyber: Modernizing the Security Infrastructure
This report for Sonrai Security provides important insights into the current state of public cloud security and where the most critical security gaps are found when managing legacy infrastructure. The report further provides recommendations on what actions organizations can take to reduce their risks and improve cloud security.
Download the full report: Modernizing the Security Infrastructure.
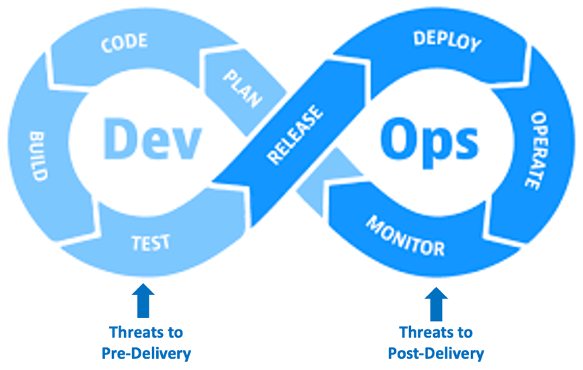
July 13, 2022
Tag Cyber: Understanding DevOps Threats
This is the first of a new five-part series of articles developed by TAG Cyber in conjunction with Sicura to offer insights and guidance into modern DevOps security using automated and integrated support.
Read the first chapter of Understanding DevOps Threats.

June 21, 2022
TAG Cyber: The Hazards of Exposure to Network Monitoring
Enterprise cyber adversaries are getting more sophisticated and aggressive, calling for more powerful defensive tools in response. Learn about stealth and obfuscation techniques, formerly only accessible to nation-state intelligence agencies, which are now available to protect commercial networks from surveillance and disruption.
SecureCo, in collaboration with TAG Cyber, has published a free e-book on Non-Attributable Data Networking and Communications.
Read the synopsis on LinkedIn.
Read the first chapter, The Hazards of Exposure to Network Monitoring.
Download the entire e-book here.

June 6, 2022
CSA: Zero Trust and the CISO
Nothing like talking about rainbows and vampires with Dr. Chase Cunningham and John Kindervag, and Jim Reavis at the final session of the Cloud Security Alliance Summit, ‘Zero Trust and the CISO’.
Read the synopsis on LinkedIn.

May 25, 2022
Tag Cyber: Today’s Third-Party Risk Challenges
Brad Hibbert, COO at Prevalent, joins John Masserini, Senior Research Analyst at TAG Cyber, in a discussion about the challenges of Third-Party risk and an overview of Prevalent’s security products.
Watch the Interview with Brad Hibbert on YouTube.

March 18, 2022
TAG Cyber: Evaluating the SentinelOne Acquisition of Attivo Networks
Conceptually, the idea behind XDR is to include non-endpoint telemetry into the risk decision-making process occurring on the endpoint. While account and identity theft remain the most attacked vector in most enterprises, the majority of EDR/XDR solutions fail to include substantial identity telemetry into the solution, resulting in coverage gaps across the entire vertical. SentinelOne’s acquisition of Attivo is a significant advancement in addressing those gaps.
Read the full analysis on LinkedIn.

February 18, 2022
Delivering Comprehensive Cybersecurity for SMBs
In this webcast, you’ll hear from industry leaders about how this partnership delivers next-generation tools allowing SMB leaders and managed service providers to meet security requirements with confidence and ease.
Meet the participants:
- Moderator: John Masserini, Senior Research Analyst, TAG Cyber
- Raffaele Mautone, CEO & founder of AaDya Security
- Julie Cullivan, C-level Global Business & Technology Operations/Cybersecurity & Independent Board Member
- Sridhar Jayanthi, Sr. VP Endpoint at EclecticIQ
Watch Delivering Comprehensive Cybersecurity for SMBs on YouTube.
Copyright © 2002-2025 John Masserini. All rights reserved.


