Estimated Reading Time: 5 minutes
Recently, Fitch Ratings issued a report on the state of the Cyber Insurance Umbrella Liability market, the significant increase in costs, and the revised expectations that most insurers have on the cyber resiliency of a customer. If you are unfamiliar with Fitch, they are a provider of credit ratings, commentary, and research predominantly focused on institutional investors.
The Role of Cyber Insurance
As any security executive will tell you, cyber insurance plays an integral role in the enterprise risk mitigation strategy. There is an old saying – mitigate what you can, accept what you can’t. That saying doesn’t explain that, in today’s world, the acceptance of significant risk is typically offset with some type of umbrella cyber insurance.
One of the things I love most about this field is that is always evolving. We battle adversaries who are constantly developing new attacks with tools that didn’t exist six months ago. It is a seemingly endless game of chess played on a board of infinite squares. So, while I thrive on the continual challenges presented by the ceaseless evolution of attacks, it also puts everyone responsible for defending an enterprise eternally behind the curve. This ‘always in catch-up mode’ quandary is less than ideal, it is, in fact, a situation security teams face daily. This gap in (security) coverage is where we see the primary use of cyber insurance.
Also, while it is sometimes difficult to admit, more often than not, there are parts of companies that we simply cannot protect sensitive information assets to an appropriate level. There are many reasons for this – contractual obligations with third parties, technology that is too outdated (aka ‘end of life’) and is no longer supported by the vendor, or when a certain piece of infrastructure is scheduled for sunset, thereby naturally limiting any further investments. Any of these reasons, and likely many more, are valid arguments as to how cyber insurance can be leveraged to offset acceptable risks within an enterprise.
Results of the Fitch report
According to the report, the cyber insurance market collects around $10 billion in premiums annually, with that expected to double by 2025. The report also highlights the fact there was a 74% growth in premiums during 2021.
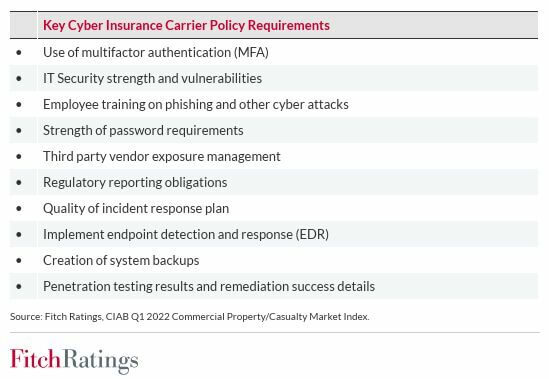
When Fitch looked into the requirements most carriers have, you see some very common, and frankly, very basic, security controls that are expected to be in place. Most carriers expect that you will be able to prove these controls are implemented and auditable – in other words, they are not just going to take your word for it.
In looking at this list, it reminded me of the OWASP Top 10. Not because it was AppSec related, but because by doing these basic ten things, you would address a lot of the systemic risks that insurance carriers are worried about. It was also very clear to me that each of these controls is directly related to one (or more) NIST CSF controls. Since you already know how I feel about the CSF, it only makes sense to tie all of it together.
The Role of the NIST CSF
Before we get into how the NIST CSF can be leveraged in obtaining cyber insurance, we need to level set expectations.
There are two key terms that sadly, are incorrectly interchanged frequently, that have a direct impact on the success a security program can quickly achieve.
Good vs. Best Practices
- Standards of Good Practice: A Standard of Good Practice is a term that generally means, as an industry, the given practice should be considered the baseline minimum process or technology implemented.
- Best Practices: A Best Practice means a technique or methodology that, through experience and research, has been proven to provide the most desirable outcome possible.
As an example, for most industries, 10 years ago, a user ID and an 8-character, mixed-case alphanumeric password was considered a Standard of Good Practice. If you had a second factor you also used when logging in, it was considered a Best Practice. However, as they do, practices evolve and today, a Standard of Good Practice includes the second factor, and the Best Practice has evolved into leveraging passwordless authentication or clandestine behavioral biometrics.
NIST CSF and Cyber Insurance Expectations
When evaluating the requirements identified by the report, associating them with the various CSF controls is fairly straightforward. While the generality of the carrier requirements leaves a bit to interpretation, we can fairly easily codify the controls into the common CSF categories/sub-categories.
In the table below, you will find the requirements identified by Fitch as well as the associated NIST CSF control references. Additionally, I’ve given some examples of Good and Best practices to be considered when you are trying to determine where along the line maturity line you are. They should in no way be considered ‘goals’ – but are here to give you some context around expectations.
NIST/Fitch Security Controls
| Key Cyber Insurance Carrier Policy Requirements* | NIST CSF Reference | Good Practice (GP) / Best Practice (BP) |
|---|---|---|
| Use of multifactor authentication (MFA) | PR.AC-7 | GP: All critical devices, remote access & SaaS access is protected by MFA. – – – BP: All user access, regardless of origin or destination, is protected by MFA. |
| IT Security strength and vulnerabilities | ID.RA DE.CM-8 | GP: Vulnerability scans are performed with ‘best effort’ mitigation. – – – BP: Vulnerabilities are evaluated based on internal risk assessments, and mitigation is prioritized and within expected timelines. |
| Employee training on phishing and other cyber attacks | PR.AT | GP: Users are trained on general phishing/cyber attacks annually. – – – BP: Customized quarterly training based on job function. |
| Strength of password requirements | PR.AC | GP: Common password requirements across all users. – – – BP: Risk-based password requirements customized based on the sensitivity of data being accessed or the criticality of services being supplied. |
| Third-party vendor exposure management | ID.SC | GP: Standard cybersecurity clauses included in contracts. – – – BP: Full inventory of third-party assets within the infrastructure. User access is managed similarly to employee access. Compliance & technical audits are performed annually. |
| Regulatory reporting obligations | ID.GV-3 | GP: Legal reporting has been formalized by policies and approved by executive management. – – – BP: Privacy, Regulatory, and Law Enforcement notification and reporting have been defined and are included as part of Incident Response tabletop exercises. |
| Quality of incident response plan | RS.RP PR.IP-9 PR.IP-10 | GP: Incident Response and Business Continuity plans are in place and reviewed/tested annually. – – – BP: Incident Response and Business Continuity plans are in place with formal semi-annual tabletop exercises for all functions. |
| Implement endpoint detection and response (EDR) | DE.CM-3 DE.CM-4 | GP: Endpoint detection solutions are installed on all user devices, with regular updates. – – – BP: Endpoint detection solutions are installed on all user and infrastructure devices, with regular updates, with centralized event/incident reporting to the Security Operations Center. |
| Creation of system backups | PR.IP-4 | GP: Backups are performed daily, validated, and tested annually. – – – BP: Backups are performed consistently, recovery is tested semi-annually, and systems can be returned to an operational state within an acceptable RTO timeframe. |
| Penetration testing results and remediation success details | ID.RA-1 PR.IP-7 PR.IP-12 | GP: Annual third-party penetration test against external-facing infrastructure. – – – BP: Continual penetration testing of all internal & external environments. Results fed into the development lifecycle and risk assessment process. Vulnerabilities resolved prior to production deployment. |
* – As defined by the Fitch report
Conclusion
Hopefully, this will provide some insight into how to qualify for cyber insurance or lower your existing premiums. While none of this is really rocket science, it is rather helpful to at least understand what your carriers are looking for and how you provide evidence that you satisfy the criteria. And, let’s not forget, you’ve improved your overall security posture as well.
Copyright © 2002-2025 John Masserini. All rights reserved.