Estimated Reading Time: 5 minutes
Recently, I read an article about how a CISO talked his way out of having an internal auditor write up a finding about weak passwords – which eventually lead to a significant and highly publicized breach. The CISO’s argument was that, by implementing strong passwords, users would end up just writing them down, thereby, weakening the overall security of the company. This article started a healthy debate amongst some colleagues about what risk we’re truly trying to address.
During the discussion, I questioned what ultimately is the bigger risk – the chance that a colleague would steal a password written on a sticky note, or an adversary would toss a rainbow table full of common words at a weak password and crack it in seconds.
I would certainly never second-guess a fellow CISO – and this is simply just something to think about – but at the end of the day, who are we actually trying to protect ourselves from? Sure, there could be the rouge cleaning person who steals the sticky note, but at the end of the day, isn’t the electronic threat far more worrisome than the physical one these days? There is an old adage in the industry that people are the weakest link. No matter how many controls you put in place, a person will give up their password in a heartbeat if threatened with blackmail or violence.
For decades, we’ve had the ‘don’t write passwords down’ mantra drilled into us, and in turn, drilled it into our users. But let’s be serious, is there anyone out there – CISO’s and non-security folks alike – who doesn’t write them down somewhere? Take a count of how many different passwords you have personally or better yet, count the number of times you click that infamous ‘I don’t remember my password’ link over the course of a year.
We all get heat for strong passwords, change frequency requirements, and re-use limitations, but what most end users don’t realize is, security folks hate passwords as much as users do. They provide very little peace of mind in the overall strategy of a security program, and most of us presume a user’s password could be subverted fairly easily. Sadly, it’s really all we have, so it’s what we’re stuck with. Sure, there are plenty of alternatives out there, but just say the word ‘token’ to a user and watch the glare you get; or suggest biometrics and the hair on the back of the ‘privacy empowered’ user will stand straight up.
That said, the reality is we have several awesome point solutions, but nothing that will completely replace passwords in an enterprise environment. We are challenged by the complexities of Moore’s Law, which is completely divergent with the way technology is deployed across an enterprise. I challenge anyone to convince his or her CFO to pull out hardware before it’s fully depreciated, because ‘Oh, hey, there’s better stuff today’.
If, just for a moment, picture a world without hardware and operating systems that were designed – and in some cases deployed – before many of us were born. How easy would our lives be if we didn’t have to solve security challenges that took into consideration infrastructure that was purchased when disco was all the rage or when Tubbs and Crocket set the stage for fashion?
So, how do we go about solving the Password Problem? Damned if I know.
That said, here are some approaches to consider lessening the burden of passwords on the user base, and hopefully, allowing you to adopt stronger password controls. None of them really solve the overall problem of antiquated infrastructure and outdated ‘business-as-usual’ approaches but used in combination with what we are already stuck with, we may be able to make the entire process a bit less burdensome for our user community. After all, a user-base that doesn’t see security as a roadblock is one of the best allies we have.
Approach #1: Consider approving a password-vaulting app.
Yep – you read that right. Encourage your users to write their passwords down – sort of. With the number of apps available for iPhone and Android, why not take advantage of it? We all know users who would turn around and drive back home to get their phone but would never do that if they forgot their ID badge. Why not find and approve a password-vaulting app that users are encouraged to install on their phones? Perhaps roll it out with stronger password requirements, encouraging your users to use the app as a way to remember the stronger passwords.
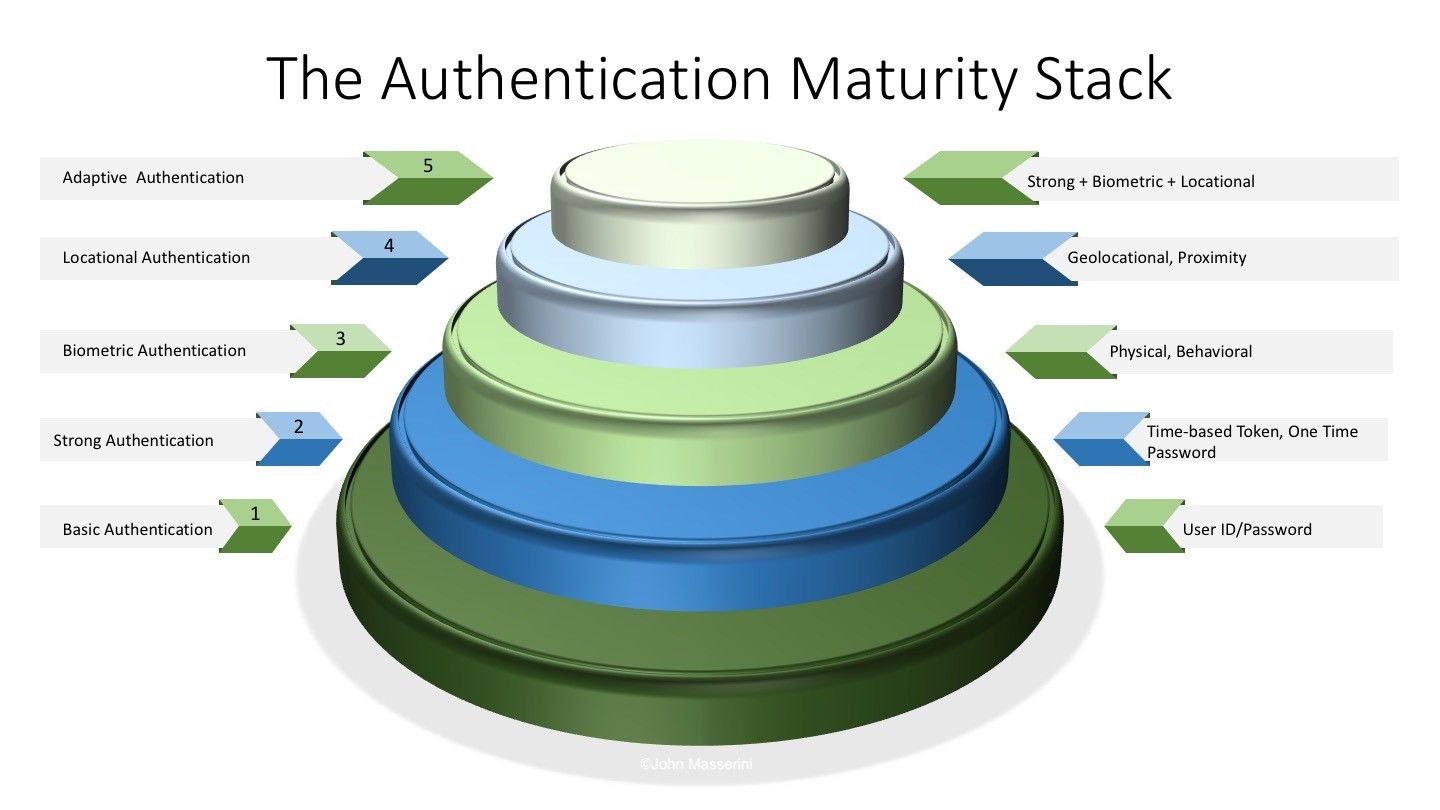
Approach #2: Adaptive Authentication
No – this does not mean easy, static passwords for the Executives and strong, cumbersome passwords for everyone else. If you were to look at your average user’s daily workflow, you would find that the majority of the time, they do not deal with highly sensitive information or access critical systems on a continual basis. If that’s the case, why make them go through a virtual cyber-TSA checkpoint just to check email or browse the web? Adaptive Authentication allows you to increase the level of authentication requirements based on the properties of the application or data elements being accessed. Need access to your desktop? A simple password may do the trick. Want to update the financials? Perhaps you need a strong or one-time password in addition. Want to download your employee’s files? Sorry – biometric access only. Adaptive Authentication provides you the ability to protect the most critical information assets without enforcing a ‘War and Peace’ length credential when it’s not necessary.
Approach #3: RFID tag them
Sadly, we can’t RFID tag our users… yet. (But if you’re interested to see how close we are, check out the now-defunct VeriChip). But how about tagging the next best thing – once again – their phones. There are several solutions available today that allow you to place a small RFID sticker on the back, or inside the cover, of a mobile phone. When the phone comes within a certain distance of the workstation, the workstations read the tag and allows them limited access to the desktop. Move the phone out of the RFID range and the desktop locks. By layering an Adaptive Authentication solution over top of the RFID tag, you can require progressively stronger passwords based upon the sensitivity of the application or data. Want access to your desktop? Perhaps the RFID authentication is good enough. Want to review the M&A targets for next year? You’ll need the RFID tag and a one-time password. Want to review the salaries of the entire executive team? RFID tag, one-time password, and MAC address verification are the mandates.
(Side note: There are a few Bluetooth solutions that work the same way as an RFID tag, but the results seem to be mixed based on hardware compatibility. I’d keep an eye on the technology though – it may be a solid solution near term).
Approach #4: Text
I’m not sure about you, but the best way to reach my retired parents these days? You guessed it – I text them. Today, texting has become the communication vehicle of choice for young and old alike – and everyone in-between. Most major financial institutions offer text updates for large balance changes, suspected fraud activity, and weekly account recaps, so why start using text messages to replace the necessity of passwords? There are a number of partners, from Cloud WAF providers to firewall manufacturers, who integrate with hardware and software solutions to provide SMS functionality to an enterprise. Again, layer this with a basic Adaptive Authentication solution and you’ve got a pretty slick way to make your user’s life a bit easier.
Some final thoughts. We need – as an industry – to find a way to wipe the plight of passwords off of the security continuum forever. Just as we’ve developed statins to limit the amount of cholesterol in our bodies, we need to be creative and develop better ways to address the ongoing disease of password-proliferation. None of these approaches will permanently solve the problem, but they do go a long way in enhancing the user experience while reducing the risk associated with weak passwords – and honestly, how often do we get to say that?
For more on Identity and Access Management, view these articles.
Originally posted on SecurityCurrent.com.
Copyright © 2002-2025 John Masserini. All rights reserved.