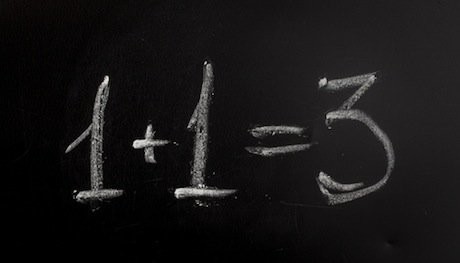
Estimated Reading Time: 6 minutes
Some time ago, I had a moment of introspection, which oddly, sounded a lot like Redd Foxx, in his best deadpan Fred Sanford delivery…. ‘It’s the privileged user …. Dummy!’
Those of us who have been in the space for a while recognize the one common factor in every significant breach is the abuse of privileged accounts throughout the kill chain. Whether it’s a local windows admin account used to install the malware, or truly owning a server’s root account allowing the attacker full access, privileged accounts are critical for a successful breach to occur.
Holistically, as an industry, we have continually moved from the outside in. Decades ago, we focused on the external networks, protecting the soft inside with a hard exterior shell. Over time, that focus moved to the internal networks, then the application layer, and then to the storage layer, always chasing the attack vector or exfiltration method rather than focusing on the kill chain. At the end of the day, however, without user credentials, the attacker’s life is immeasurably more agonizing.
While gaining access to privileged user credentials is one of an attacker’s primary objectives, identifying the difference between normal user behavior and suspect activities has always presented a unique challenge in security analytics. By definition, admins are often expected to be able to ‘go anywhere – do anything’ in order to be able to, with a few deft keystrokes, get the production system back online or install that piece of code that is critical for the business. Admins are the key to a successful operations environment.
So how, from a monitoring or predictive analytics perspective, is InfoSec supposed to monitor the use of such accounts without being the reason the production system was down for an extra five minutes?
I think the time has finally come.
Over the past 12 months, an interesting congruence has occurred between two distinct solution sets – the operational controls of the stalwart Privileged Access Management (PAM) and the bleeding edge algorithmic modeling of User Behaviour Analytics (UBA).
PAM is the management and control of user accounts that have elevated or privileged access to various systems. Typically, these are perceived to only be ‘root’ or ‘Administrator’ accounts, but in reality, these are any accounts that have the ability to change a configuration, install/delete software, or provide access to information that they would otherwise be precluded from accessing. Although historically, PAM was a ‘we offer that too’ solution proffered by a number of vendors, recently it has become a major focus for organizations due to the realizations that many of the publicized breaches over the past 18-24 months have had some aspect of privileged account abuse as part of the attack.
UBA is the algorithmic modeling of user behavior over a given time period and comparing that behavior to future activities in the hopes of identifying miscreant activity. Unlike a typical Security Event/Incident Monitoring solution, which focuses on the aggregation and correlation of events, UBA products continually re-evaluate current and historical events recursively, improving the future state of the model.
The theory behind UBA is that when the attackers obtain access to an infrastructure, the first thing they go after is the privileged accounts in order to ensure their long-term presence in the systems. By abusing such credentials, they can install rootkits, hidden malware, and any other suite of tools they may need to ensure they get – and keep – system access. By comparing the original ‘clean’ user model to future activities performed by the account, deviations can be used as indicators for the security team.
While the UBA space is somewhat nascent, there has been a tremendous amount of effort put into developing some fairly complex algorithmic models to address the inconsistencies of the various enterprise environments. In fact, the UBA space is expected to have a compound annual growth rate of 100% over the next few years, going from $50 million to over $200 million by 2017.
Most industry experts argue that a breach is unavoidable and we need to focus on rapid detection and limiting the extent of the breach. Given that, how can we leverage the salt-and-pepper haired maturity of a PAM solution with the hot and sexy techno of UBA to provide our teams with rapid detection and protection of our critical assets? Is it even possible to model user behavior if there is a lack of trust in the environment they are working in? Can an existing, legacy infrastructure adequately model user behavior to a granular enough level that the information is useful to the InfoSec team?
I believe we can, and in fact, we must.
The entire concept of managing privileged access treads into the forbidden woods of most IT organizations. When a PAM solution is introduced, likely the very first question is “Why? don’t you trust the admins?” The reality is it has nothing to do with the admin, either personally or professionally. It does, however, have everything to do with their system credentials. We have to get beyond the trust discussion and really have an open dialog about risk – the risk they take surfing the web, opening up the email from the unknown sender, or installing that app downloaded from who-knows-where.
To be honest, I completely trust the admins I work with every day, but that doesn’t change the fact that we have built an in-depth control structure around their access. That said, they also understand that their god-like superpowers in our environment make them a legitimate target for the bad guys, and frankly, the last thing they want is their account – their system – their reputation – associated with a breach. There is also a concern around something ‘getting in the way’ of an admin and theoretically hindering their ability to resolve an issue. The truth is, when deployed correctly, there is no higher probability of this occurring with a PAM than without.
The migration to a PAM solution provides something that you very rarely get these days – a chance to start fresh. A majority of the work involved with deploying a PAM infrastructure typically revolves around verifying system access and configuring such access in the solution. Generally, this involves reviewing all-access credentials to the various system and verifying the authorized users have appropriate levels of access. This also provides you a perfect opportunity to begin monitoring each system with a UBA tool as you now have a clean starting point associated with those credentials. If, as in many places, the approach to a PAM rollout is slow and methodical, then by following parallel paths, you can have a fully functional UBA solution as you finish up the PAM deployment. While this is perhaps a nirvana-type approach, it doesn’t mean that you cannot achieve the same end goal if you already have a PAM in place.
One key aspect of a UBA deployment is the time needed to model the user base. Typically, this is in the 60-90 day period before you have a level of assurance that you are seeing everything a user does. Remember, as with any type of analytics process, the longer the model runs, the better the predictability and the stronger the reliance that can be placed on the outcome. While most UBA solutions can start alerting on questionable behavior within a few days, the long-term results will be far more actionable. If you think about how your workplace functions, there are likely monthly/quarterly/annual activities that will eventually make it into the model, so when Sally from Finance accesses that reporting server the 3rd day of every month, it will be treated as normal and not cause a false-positive alert.
This ‘Time to Learn’ is a key aspect to consider when deploying a UBA solution. Does the tool model other similar users in order to detect what is normal for the group compared to the individual? Is there one Windows Admin who logs into a Linux box every day at 2am, but none of the other Windows Admins do? While it could be a legitimate activity, it could also be an indicator of someone doing something malicious… Only ‘Time to Learn’ will tell.
That said, it is the intersection of these two solution sets that truly provides a level of user-associated risk mitigation that many of us strive for. Whether dusting off your ‘installed-but-rarely-used’ PAM solution or implementing one fresh, the relationship between it and UBA cannot be overstressed. While both PAM and UBA solutions have their individual merits, from an overall risk perspective, the benefit of both far exceeds what even most vendors perceive as value. Understanding that UBA is most beneficial when it can model clean accounts, and knowing how to leverage a PAM solution to ensure it is, results in one of the rare opportunities when One plus One actually does equal Three.
Fred Sanford was right..
For more on Identity and Access Management, view these articles.
Originally posted on SecurityCurrent.com.
Copyright © 2002-2025 John Masserini. All rights reserved.