
Estimated Reading Time: 4 minutes
The very first piece I had published was in 2002 for the International Association of Privacy Professionals newsletter, discussing how secure enclaves would be beneficial to the privacy effort. The newsletter is no longer published, so I have re-published the original piece here.
Ensuring Privacy through Secure Enclaves: Secure Architecture Designs that Enable Privacy
For years, security experts have been evangelizing the benefit of replacing the monolithic “go everywhere-and-do-everything” network paradigm with one that is more activity-focused and business-centric. By breaking up the wide-area network into smaller, more manageable chunks, or enclaves, network and security administrators could tailor the authentication and authorization controls to the specific business needs while limiting the overall risk to the organization. Recently, however, the secure enclave effort has gained momentum as a way to satisfy several of the requirements set forth by the recent wave of privacy regulations. In this article, we examine the potential benefits of secure enclaves and how they can address some of the privacy issues faced in today’s networked environments.
The Ever-Expanding Network:
The network environment has changed dramatically over the last several years. Where once it was the norm for organizations to be totally cut off from the outside, the opposite is the case today. Collaboration, outsourcing arrangements, and other types of business partner connections all have opened up the infrastructure to unknown and untrusted, entities. Dedicated, persistent connections from external networks to a company’s infrastructure potentially open channels for breaches in security and privacy that were never previously considered to be a threat. With the varied and often uncontrollable aspects of business partner connections, coupled with the ongoing struggles of securing the infrastructure from insider threats, secure enclaves are getting more attention as a beneficial and cost-effective solution to security and privacy concerns. This can be especially important for financial services institutions that are outsourcing more technology functions and need to find effective ways to address Gramm-Leach Bliley Act (GLBA) security guidelines.
Secure Enclaves — A Background:
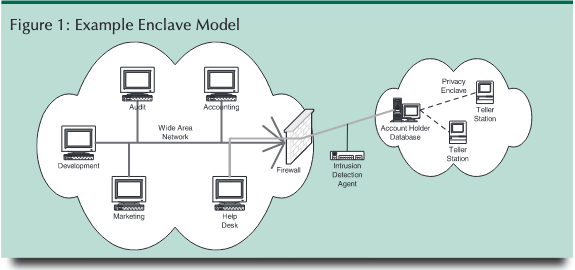
In general, enclaves are areas of the network that are segregated from the rest of the network for bandwidth, accessibility, or security reasons. For example, applications developers may have a small, segregated network that is cordoned off from the rest of the network to protect the production environment from untested code. Secure enclaves are areas of the network that are protected over and above the rest of the trusted network. This protection may include devices like firewalls or routers, strong authentication, or even fully encrypted network traffic. The process of determining the requirements of a secure enclave typically involves performing a risk analysis to identify the potential overall risk to the organization and protecting the enclave accordingly. This risk analysis, when incorporating the privacy requirements of an organization as they are supported by security policies and controls, could identify and facilitate the creation of “privacy enclaves” as a way to meet the goals and objectives of the company’s privacy policies.
Privacy Enclaves — A Solution Whose Time has Come:
Just as the need for additional security spawned the development of secure enclaves, the need for additional privacy controls on information use and disclosure is causing enterprises to evaluate the need for privacy enclaves. This is particularly the case in organizations with data that are regulated through required administrative policies that define business rules for information use and man-dated frameworks for implementing appropriate security controls. For example, section 501(b) of GLBA calls for financial institutions to ensure security and confidentiality, protect against anticipated threats, and protect against unauthorized access. By leveraging an appropriately designed privacy enclave, a financial institution could meet the requirements of all three of these directives with a relatively negligible expense and resource expenditure. For example, suppose that a privacy enclave could be developed that would segregate the account holder’s information from the rest of the institution’s user and server populations. The account holder enclave would be protected by a firewall, limiting access to the account holder’s information to only those authorized to have such access. If necessary, the traffic behind the firewall could be encrypted in addition to encrypting the records while in storage. Additionally, an intrusion detection system agent could be deployed to monitor access attempts to the information, alerting network administrators, and creating a log to document compliance efforts. If we again look at 501(b), the encryption will address the security and confidentiality requirement, the intrusion detection agent will satisfy the anticipated threats obligation and the firewall will protect against unauthorized access.
Conclusion:
If the enclave model were extrapolated to encompass the entire organization, the level of security and privacy could substantially increase. For example, published reports confirm that the majority of breaches still occur from internal users rather than outside attackers. Because of its segregation and additional security, the enclave model could provide a stronger protection against internal threats. Additionally, recent Federal Trade Commission actions are directly tied to internal misuse of private data. The enclave model offers more localized control within the organization over the implementation of security policies and data management, thereby providing tighter accountability and mitigating against inadvertent violations of policy or disclosures of data. By controlling internal access to regulated information through an enclave model, significant gains can be made in protecting private information from both intentional and unintentional disclosure. The enclave model thus offers a potentially strong option for institutions that are working to implement a cost-efficient and effective privacy and security management.
For the full article, download the PDF file here:
Copyright © 2002-2025 John Masserini. All rights reserved.