
Estimated Reading Time: 3 minutes
Consider this if you will, that at the end of 2015, Google estimated there were 1.4 billion Android devices in use worldwide, and its over 2 billion devices when you add in Apple, Microsoft, and the balance of the others.
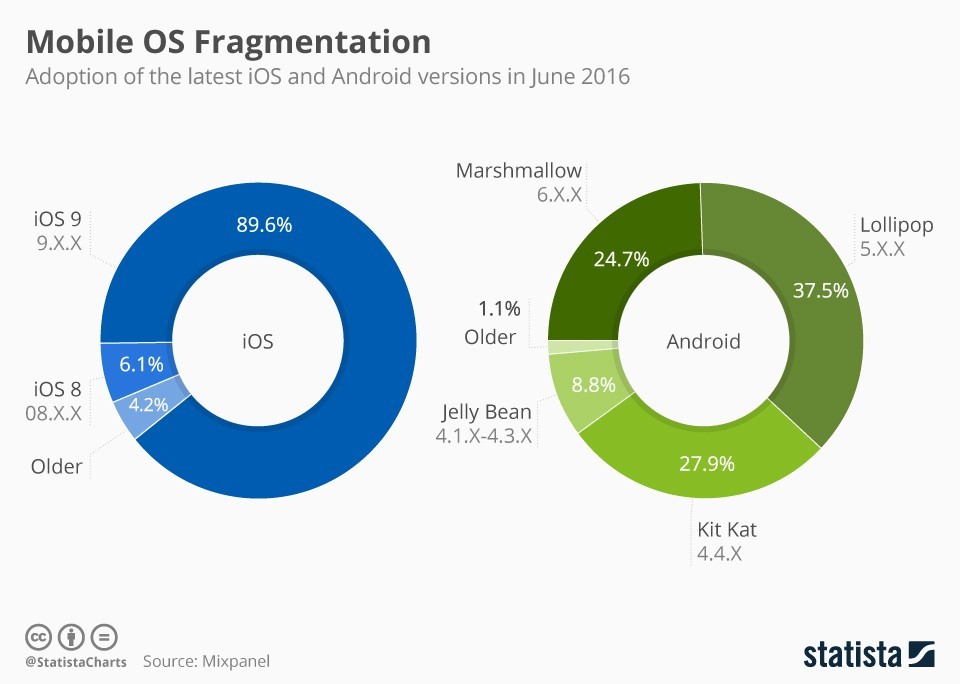
Now, think about those 1.4 billion devices – the vast majority of which are vulnerable to the ‘GODLESS’ malware that was uncovered last week. According to the TrendMicro report, 90% of all Android devices are vulnerable. The reasoning behind this is because every device that is running a version of Android that is 5.1 or older is vulnerable to two pretty nasty exploits (CVE-2014-3153 and CVE-2015-3636). While that number seems a bit high, and admittedly they are quoting their own empirical numbers, the data from Statista is close enough to Trend’s to have you running back to your Nokia 1100.
Starista Mobile OS Fragmentation
Based off of these numbers, over 1.05 billion (75%) devices are potentially susceptible to GODLESS, with almost 900,000 devices already infected. Just stop and contemplate that for a moment. As security professionals, stop and think about the potential impact that over one billion infected devices could have.
The Internet of Things isn’t coming – it’s already here – and it wants to play rough.
While the current edition of GODLESS basically just steals credentials and installs some ‘innocent’ apps, it doesn’t take much imagination to see where this could end up. Just think about the DDoS that could occur – mobile devices on Wifi hotspots around the globe, all pointing at your infrastructure, or worse, using your infrastructure to be part of the attack. Think about how many of your employees are running Kit Kat or Lollipop who regularly access your corporate infrastructure. Logging into some internal web app, or reading some sensitive document, likely using their same passwords for their work accounts as they do for their personal ones, and all conveniently centralized on their GODLESS-laiden mobile phone. Gotta love technology.
Here’s an interesting rub on those statistics though. Since the phone companies make it so enticing to get your new phone every 2 years, the old, outdated operating systems are not as rampant in North America as it is elsewhere in the word. While that may not provide any contentment to global organizations, it does offer a bit of solace to domestic-only companies.
Let’s face it though, not much will likely happen. While there have been some interesting studies around the entire ‘BYOD’ movement failing in both cost savings and productivity increases, its highly unlikely anyone who already allows such devices on their infrastructures is going to get them back out. You can’t unring a bell and you can’t de-BYOD your enterprise.
At the end of the day, it’s all about a cautious approach to the data that’s accessible on these devices and how they are controlled. While you can’t force a user to upgrade, your can lock them into limited-function networks or deny them access to certain data elements.
The perimeter is long gone, you better get creative – fast.
- ‘GODLESS’ Mobile Malware Uses Multiple Exploits to Root Devices: http://blog.trendmicro.com/trendlabs-security-intelligence/godless-mobile-malware-uses-multiple-exploits-root-devices/
- “Godless” apps, some found in Google Play, can root 90% of Android phones: http://arstechnica.com/security/2016/06/godless-apps-some-found-in-google-play-root-90-of-android-phones/
Copyright © 2002-2025 John Masserini. All rights reserved.